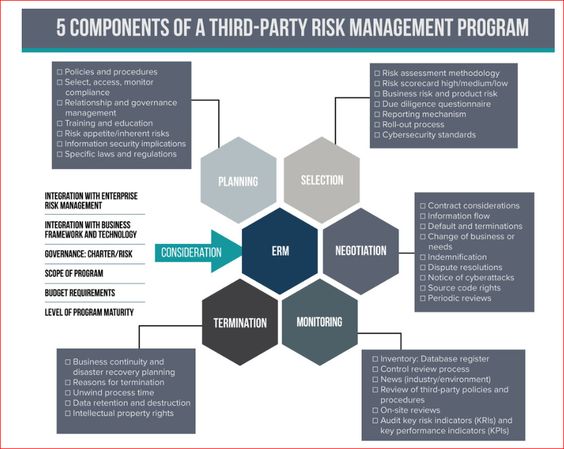
What is Risk Management of Digital Information?
Introduction
Why is Risk Management of Digital Information Important?
In today’s digital age, the management of digital information has become a critical concern for organizations of all sizes and types. The increasing volume and complexity of digital data have created new risks and challenges that require effective risk management strategies. In this article, we will provide an overview of the risk management of digital information and its importance.
Information Security Policy
Risk management of digital information is the process of identifying, assessing, and managing the risks associated with the creation, storage, processing, and transmission of digital data. It involves implementing appropriate risk management strategies to minimize the negative impact of potential risks and ensure the confidentiality, integrity, and availability of digital information.
Risk Assessment
The risk management of digital information is critical for organizations because it helps to protect their sensitive information from unauthorized access, modification, or disclosure. By identifying and managing risks, organizations can minimize the risk of data breaches, cyber-attacks, and other digital threats that can result in financial loss, reputational damage, and legal liability.
Threat and Vulnerability Management
The first step in the risk management of digital information is to establish an information security policy that defines the organization’s security objectives and the measures that will be taken to achieve them. The policy should be aligned with the organization’s overall strategy and should be communicated to all employees and stakeholders.
Access Control Management
The second step is to conduct a risk assessment to identify the potential risks and vulnerabilities associated with digital information. The assessment should consider the confidentiality, integrity, and availability of the information, as well as the impact of potential risks on the organization.
Incident Management
The third step is to implement appropriate threat and vulnerability management strategies to mitigate the identified risks. This involves implementing security controls to prevent and detect potential threats, such as malware, phishing, and social engineering attacks.
Business Continuity and Disaster Recovery Planning
The fourth step is to implement access control management strategies to ensure that only authorized individuals can access and modify digital information. This involves implementing appropriate access control mechanisms, such as passwords, two-factor authentication, and role-based access control.
Compliance Management
The fifth step is to establish an incident management process to respond to security incidents and breaches promptly. This involves developing incident response plans, testing them, and training employees to respond to incidents effectively.
Training and Awareness
The sixth step is to develop business continuity and disaster recovery plans to ensure that critical digital information can be restored in the event of a disaster or disruptive event. This involves developing backup and recovery plans, testing them, and ensuring that they are regularly updated.
You might find these FREE courses useful
Continuous Improvement
The seventh step is to ensure that the organization’s digital information management practices comply with relevant legal and regulatory requirements, such as data protection and privacy regulations.